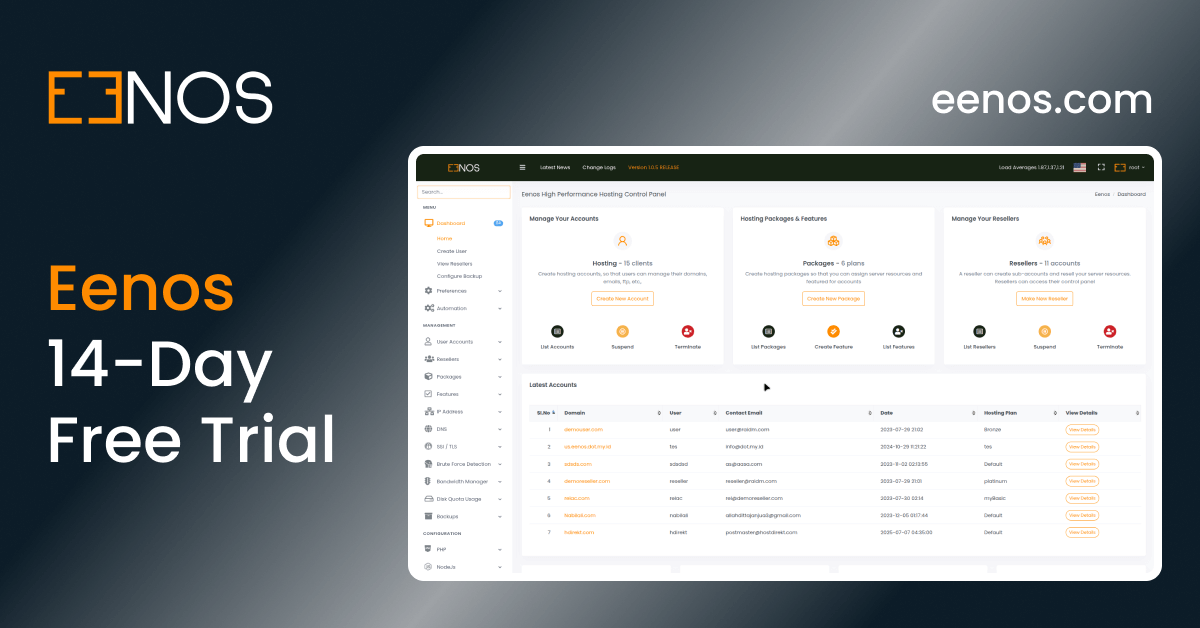
- Home
-
Features
-
Traditional Hosting
Enjoy traditional web hosting made easy with Eenos - reliable, secure, and simple management with modern tools.
-
AI & Data Analytics
AI & Data Analytics with Eenos for smarter insights and automated decisions.
-
SandBoxed Apps
Deploy sandboxed apps with Python, Ruby on Rails, and Node.js on Eenos.
Why Migrate to Eenos?
- Easy Migration Tools
- Easy Website & Domain Management
- One-Click SSL & Security
- Customizable Themes & Templates
- Automated Backups & Recovery
- Reseller & Sub-reseller Support
- Eenos Apps & Plugins
- Integrations & APIs
- Resource Monitoring & Analytics
- Branding Management
- Scripts & Tools For Automation
- Auto Updates
-
- Pricing
- Resources
- Demo
- Contact